The other day, a colleague asked how I host my website, danbrown.co, which sparked an idea – why not share the details for anyone curious? Let’s dive into the setup that keeps my website running smoothly (mostly) and securely (for now).
While many security professionals might gasp at detailing my website’s topology online, I’ve convinced myself that I must not rely on security through obscurity. I’ve ensured that there are numerous additional security measures native to the CMS, beyond what AWS and Cloudflare offer, and I trust hope they are configured well.
The Pillars of My Setup
The core of my website operates on an Amazon EC2 instance with an Ubuntu server. It’s where WordPress, SQL, Apache, and LiteSpeed Cache all come together to deliver this content to you.
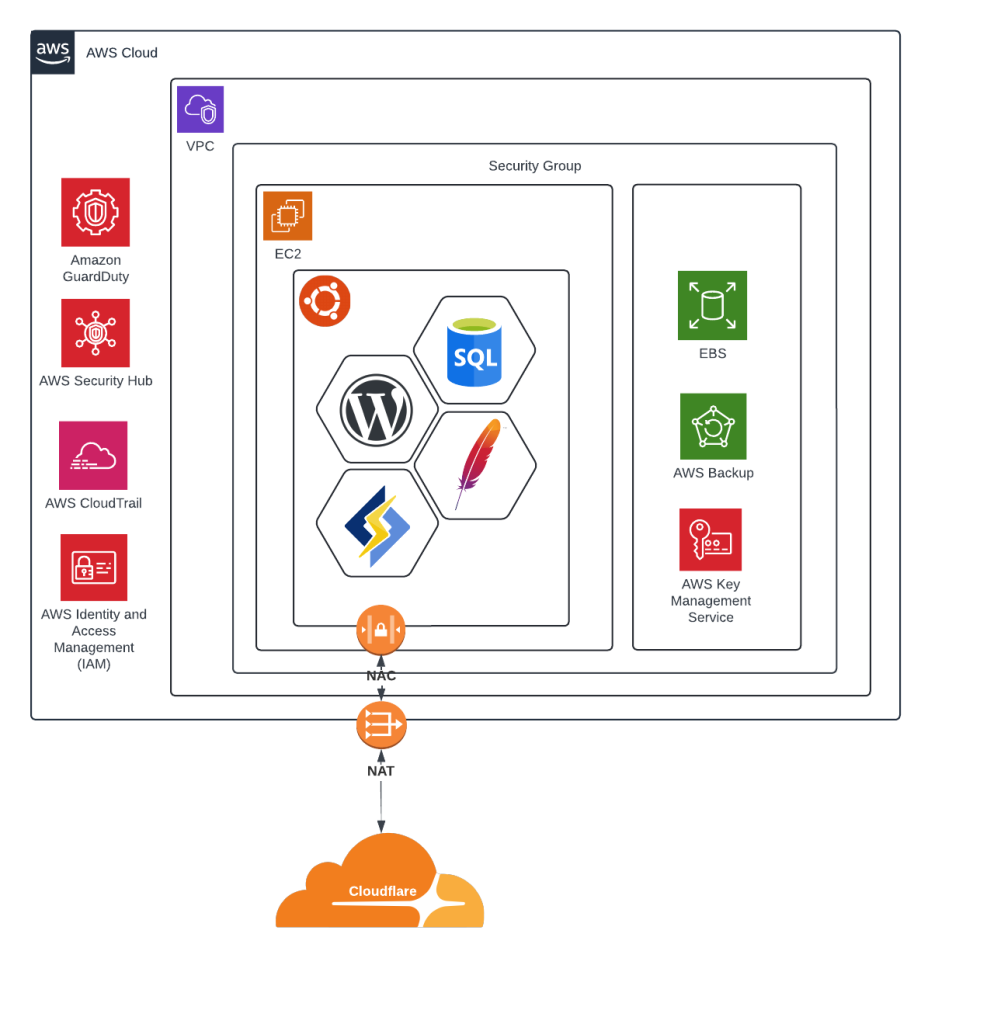
The EC2 instance is a virtual server that the Ubuntu OS runs on. WordPress is the brain that controls content management. MySQL is the database management system that stores the website data. Apache handles all the HTTP requests, making sure every visitor gets what they came for. Then there’s LiteSpeed Cache, used to accelerate and optimise content delivery so this website loads as quickly as possible.
Ensuring Smooth Operations with Storage and Backup
Now, the EC2 instance needs storage – reliable and scalable storage, hence the Amazon Elastic Block Storage. But what if the machine hits a snag? That’s where the backup strategy kicks in.
Every six hours, a backup process ensures there are eight warm copies ready for a quick restoration. For a long-term perspective, I have a 30-day cold storage system, making sure older backups are available, but lest costly to store.
Fortifying with Security Layers
Security is most likely what you’re going to be interested in so here we go.
Origin Server Security
The Ubuntu server is hardened to the CIS (Center for Internet Security) Level 1 standard, ensuring it’s robust against common vulnerabilities. Livepatch is also configured which eliminates the need for downtime by patching kernel vulnerabilities while the system is still running – so I can just patch automatically when an security update is released. Additionally, AWS Key Management Service (KMS) securely handles cryptographic keys, primarily for SSH.
Network Security
At the front line of the console, we have AWS Identity and Access Management (IAM), with a heavily limited account compared to root permissions on the AWS console.
Each server resides in its own security group inside the Virtual Private Cloud, with tight whitelisting to ensure minimal exposure. SSH access is normally disabled, but when needed, I enable it temporarily via the console and restrict it to my current IP address.
Both the edge server (LiteSpeed Cache) and the origin server (Apache) have established trust with Cloudflare using TLS, ensuring secure and encrypted communication between the servers and Cloudflare, even if I need to take the edge server out of the equation.
Web App Security
Cloudflare adds an essential layer for web app specific traffic. The Web Application Firewall safeguards against common web threats, such as SQL injections and XSS attacks. By default Cloudflare also includes comprehensive DDoS protection, shielding the website from resource attacks.
Cloudflare also operates as the authoritative DNS server for the domain.
Staying Vigilant with Monitoring and Incident Response
Monitoring is crucial. AWS CloudTrail records every action taken across the AWS environment. CloudWatch Alarms function as the alarms that go off the moment something fails, ensuring real-time responses to potential issues.
Amazon GuardDuty continuously monitors AWS for vulnerable configurations or suspicious activity. AWS Security Hub brings all the alerts and findings to a central command centre, making it easier to manage and respond efficiently.
Why This Approach?
That’s it! I recognise there are simpler ways to host a WordPress site, but this setup keeps me on AWS even though my current role primarily involves Azure and Oracle Cloud.
Beyond gaining expertise, I find creating, changing, and maintaining this website a great way to learn new things that I might not have otherwise encountered. I encourage all security professionals to step outside their usual realms and try some development outside of PowerShell and Python scripts; it can be incredibly rewarding and educational.
On Another Note
If you happen upon this blog post and find that my website has been defaced, well, that might be a cue that I need to tighten up my web app security skills a bit more!
By sharing this, I hope to provide some useful insights into cloud security and architecture.
Feel free to explore the site, and don’t hesitate to reach out if you have any questions or just want to chat about security.

Leave a Reply