As the threat landscape evolves and compliance requirements on organisations grow, senior management often finds itself with an ever-increasing cybersecurity spend that fails to mitigate threats effectively. The necessity for a proactive and cost-efficient defence strategy thus becomes more pressing than ever. Operationalising threat informed defence can bridge the gap between strategic intent and operational effectiveness, providing a structured methodology for navigating today’s complex threat landscape.
In Part 1: Maximising Cybersecurity ROI with Threat Informed Defence, we explored how adopting a threat-informed defence strategy can maximise your cybersecurity return on investment (ROI). This article outlines a detailed framework for Collecting and Analysing Adversarial Behaviours and Normalising and Prioritising Threat Data.
Collecting and Analysing Adversarial Behaviours
To effectively defend against cyber threats, understanding our adversary’s behaviours is paramount. This journey begins with the concept of the Threat Intelligence Pyramid of Pain—a framework that categorises the types of indicators defenders can use and the relative effort required by adversaries to bypass them.
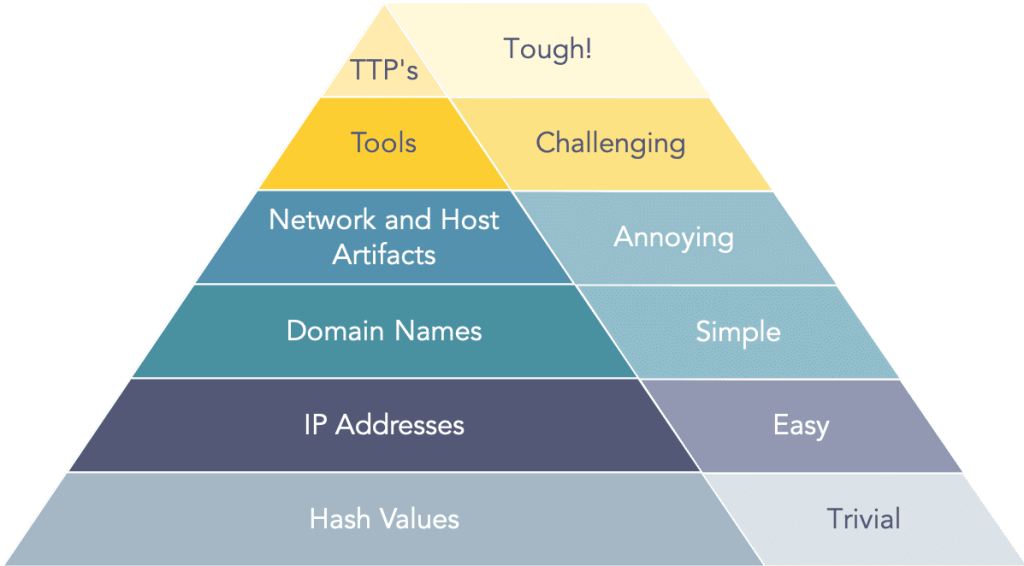
The lower levels of the Pyramid of Pain—hash values, IP addresses, and domain names—are easy to collect and apply but offer limited long-term value. These static indicators are ephemeral; they can be altered by adversaries in an instant, providing a fleeting defence.
However, as we ascend the pyramid, we encounter more valuable but harder-to-collect indicators, such as Tactics, Techniques, and Procedures (TTPs). Understanding these elements is akin to learning the playbook of our adversaries. While they require more effort to uncover, they provide a richer context for defence. Tools and TTPs are much harder for adversaries to change quickly, making them a resilient foundation for security strategies. By prioritising these higher-level indicators, we gain insights that enable us to anticipate and disrupt adversaries’ actions more effectively.
Strategic Intelligence: The Business Perspective
Strategic intelligence identifies the areas that, if compromised, would have devastating effects on the business—these include financial impacts, the trust of clients, and regulatory repercussions. Tactical intelligence, on the other hand, dives deep into the specific methods adversaries might use to exploit vulnerabilities in these critical areas.
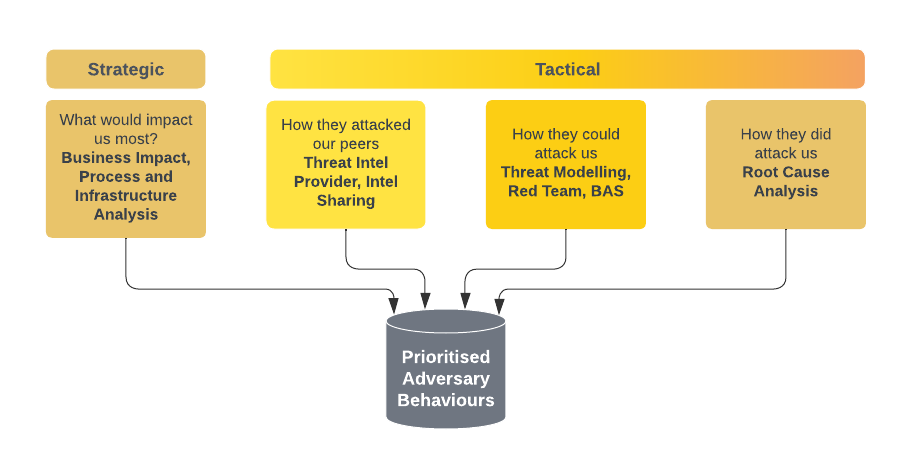
At the strategic level, the focus is on understanding and mitigating the risks that could cripple the organisation. This involves evaluating the potential financial impact of various security events, assessing how they might erode client trust, and considering the regulatory consequences of breaches.
Understanding the operating environment is the foundation of strategic intelligence. This encompasses not only IT relationships but also the broader business relationships that could influence security. Cybersecurity efforts should not be siloed; they must consider all facets of the organisation.
From an IT perspective, this means stepping back from just thinking in terms of infrastructure topology and instead focusing on workflows:
- What applications do users employ?
- What data do these applications process?
- What infrastructure supports these applications?
This approach creates an abstract, yet comprehensive, conceptual framework. This helps bridge the gap between tactical and strategic considerations by providing a detailed understanding of the operating environment.
This holistic view facilitates prioritisation by highlighting which parts of the business are most critical and therefore most in need of protection. It’s the starting point for a strategic process that narrows the focus to the most crucial security events that could impact the business.
Strategic intelligence serves as the compass for our tactical efforts. By identifying the areas with the highest potential impact, it allows us to weight different elements of our tactical intelligence appropriately. The result is a finely-tuned defence strategy that aligns with the organisation’s overall risk management goals.
Tactical Intelligence
While strategic intelligence gives us the big picture, Tactical Intelligence involves zooming in on our adversaries, dissecting their tactics, techniques, and procedures (TTPs). Think of it as getting into the mind of a master criminal, understanding their methods to predict and counter their moves.
How They Attack Our Peers: Using Threat Intelligence Platforms
One of the keys to effective defence is learning from others’ battles. By examining how adversaries attack our peers, we can anticipate and prepare for similar strategies.
One of the most effective ways to gather this intelligence is through a threat intelligence provider. Imagine a vast network of informants spread across different cities, providing real-time updates on criminal activities. This is what a Threat Intelligence Platform (TIP) does for us. These platforms integrate data from various sources, offering a detailed view of adversarial activities targeting our industry and geographic peers. By analysing these patterns, we gain invaluable insights into the TTPs employed by threat actors, allowing us to fortify our defences accordingly.
How They Could Attack Us: Threat Modelling and Simulation
Understanding how adversaries could attack our own organisation requires an introspective approach. It’s like setting up mock scenarios to anticipate and prepare for real threats.
Threat Modelling
Think of threat modelling as a war game. Here, we gather critical personnel and stakeholders to explore various attack scenarios. It’s a brainstorming session that translates into attack trees and heatmaps, pinpointing potential vulnerabilities in our systems. This isn’t a mere academic exercise; it’s about preparing detailed plans to strengthen our defences, ensuring we’re not caught off guard.
Red Teaming
Red Teaming exercises are our undercover operations where we simulate real-world attacks to test our defences. Skilled professionals assume the role of adversaries, probing our systems for weaknesses. It’s akin to hiring a former burglar to assess the security of your home—it’s intense, revealing, and extremely effective.
Breach and Attack Simulation
Platforms like AttackIQ, Pentera, or Cymulate allow us to simulate breach scenarios continuously. These are like flight simulators for cybersecurity, putting our systems through rigorous tests to validate our security controls. This way, we’re not merely assuming our defences are robust—we’re proving it through continuous testing.
How They Have Attacked Us: Learning from Past Incidents
Reflecting on past incidents is crucial for improvement. Whenever an incident occurs, we perform a thorough Root Cause Analysis. It’s a deep dive into the specifics of the breach, identifying the exact techniques used by attackers. This process is vital for updating our threat models and reinforcing our defences. Each RCA is like a case study that provides lessons for enhancing our cybersecurity posture.
Normalising and Prioritising Threat Intelligence
The practice of normalising and prioritising threat intelligence is a cornerstone of an effective threat informed defence strategy. It involves taking numerous sources of tactical intelligence and converting them into a common framework—in this case, MITRE ATT&CK techniques and sub-techniques. This allows us to create a unified view, making it easier to compare and analyse the data.
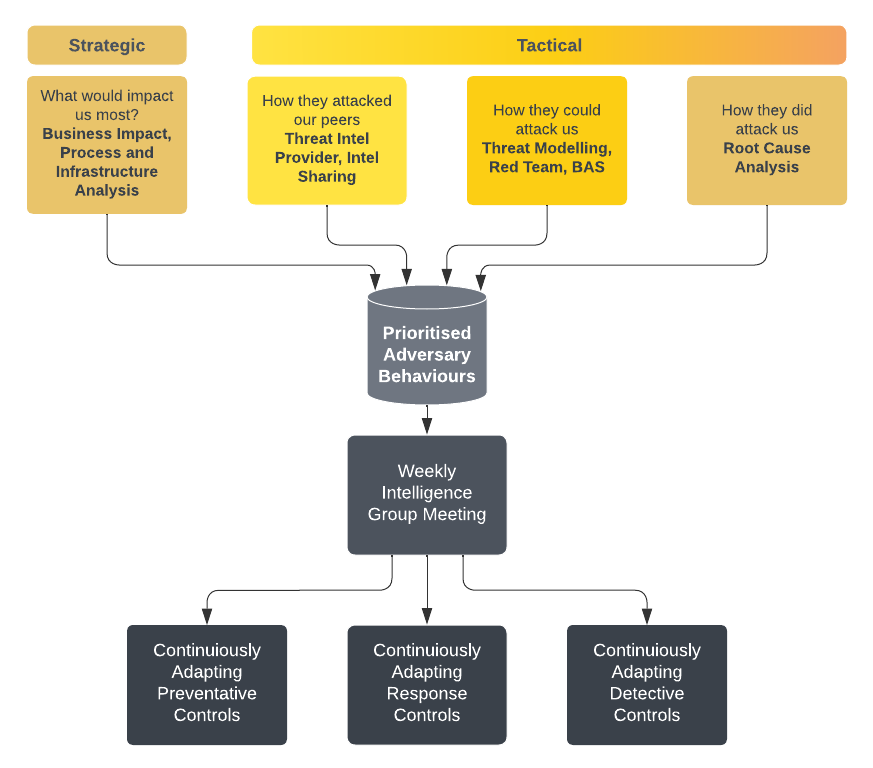
Normalising Tactical Intelligence
The first step in this process is to normalise all collected tactical intelligence into MITRE ATT&CK techniques and sub-techniques. This is comparable to converting various languages into a single, universally understood language, enabling us to integrate insights from multiple sources seamlessly.
As we compile data from threat intelligence platforms, internal incident reports, threat modelling exercises, and other sources, each piece of intelligence is mapped to a corresponding MITRE ATT&CK technique or sub-technique. This standardisation is crucial, as it allows us to consolidate disparate data points into a coherent structure.
Once normalised, the techniques and sub-techniques must be weighted using insights from our strategic intelligence. This ensures that our defensive efforts are aligned with the specific threats that pose the most significant risks to our organisation.
For example, if we don’t have a Kubernetes environment, techniques like T1610 Deploy Container and T1609 Container Administration Command should be given lower priority. Conversely, if Active Directory is our primary identity provider, techniques such as T1556 Modify Authentication Process and T1484 Domain or Tenant Policy Modification should be weighted more heavily.
Prioritising Tactical Intelligence
To prioritise our threat intelligence, we need to calculate the frequency of each technique seen across our consolidated intelligence data. We begin by counting how often each technique appears in our threat intelligence. This provides a baseline understanding of which techniques are most frequently observed.
Next, we adjust these counts based on the weightings derived from our strategic intelligence. Techniques that align closely with high-impact strategic concerns are given higher scores. For instance, if a technique is seen frequently in the intelligence data and also has a high strategic weight due to its potential impact on critical business operations, it will receive a compounded high priority.
It’s important to note that the process for prioritising threat intelligence can and should be tailored to the unique needs of each organisation. There is no one-size-fits-all approach, and organisations must determine the best way to implement this process to suit their specific threat landscape and business priorities.
Some organisations might choose to prioritise by focusing on techniques that could have a catastrophic operational impact, while others might focus on techniques indicative of specific threat actors targeting their industry.
The key is to maintain flexibility, allowing the process to adapt as new intelligence and strategic insights are gathered. This ensures that the defensive posture remains dynamic and responsive to emerging threats.
Conclusion
Normalising and prioritising threat intelligence transforms raw data into actionable insights, guiding security teams on where to focus their efforts for maximum impact. By aligning tactical intelligence with strategic business priorities and customising the process to fit the unique characteristics of the organisation, we can create a robust, adaptive defence strategy that is both proactive and effective against the evolving threat landscape.
In Part 3, we will delve into how you can operationalise this actionable data, focusing on the creation and execution of a workflow of continuous improvement. This ensures that your cybersecurity posture remains dynamic, resilient, and ever-evolving to match the sophistication and agility of adversarial tactics. Stay tuned as we explore how to turn these prioritised insights into concrete actions that enhance your overall security framework.
FAQs
What is the Threat Intelligence Pyramid of Pain and why is it important?
The Threat Intelligence Pyramid of Pain is a hierarchical framework categorising different types of threat indicators based on the difficulty for adversaries to alter them. The pyramid ranges from simple, easy-to-change indicators like hash values, IP addresses, and domain names at the bottom to more complex and harder-to-change indicators like tools and Tactics, Techniques, and Procedures (TTPs) at the top.
Understanding this pyramid is crucial for threat informed defence because it helps organisations prioritise their focus on higher-level indicators—such as TTPs—that provide deeper insights and are harder for adversaries to modify. This prioritisation ensures a more resilient and effective security strategy.
How can strategic intelligence enhance tactical intelligence in a threat informed defence strategy?
Strategic intelligence serves as the compass for tactical intelligence by identifying the areas that would have the most significant impact on the organisation if compromised. This includes evaluating the potential financial impact, the trust of clients, and regulatory repercussions.
By weighting different elements of tactical intelligence—such as TTPs—according to their relevance to these critical areas, organisations can ensure their defensive efforts are aligned with the most pressing risks. For example, if Active Directory is a primary identity provider, techniques related to its compromise are given higher priority. This alignment enables a more focused and efficient allocation of resources.
Why is it necessary to normalise and prioritise threat intelligence, and how does this process work?
Normalising and prioritising threat intelligence involves converting all collected tactical intelligence into a common framework, like MITRE ATT&CK techniques and sub-techniques. This allows organisations to create a unified view of the threat landscape, making it easier to compare, analyse, and derive actionable insights.
The process typically involves the following steps:
- Normalisation: Mapping each piece of intelligence to corresponding MITRE ATT&CK techniques.
- Weighting: Adjusting the importance of each technique based on strategic intelligence, such as business impact and critical areas of concern.
- Prioritisation: Calculating the frequency of each technique in consolidated intelligence data and modifying these counts based on their strategic importance.
This approach transforms raw data into clear priorities, guiding security teams on where to focus their efforts to mitigate the most significant threats efficiently.

Leave a Reply