Security Researchers have discovered vulnerabilities in BitTorrent that can be exploited to run powerful Distributed Reflected Denial of Service (DRDoS) attacks that have the potential to bring down parts of the Internet.
The research, carried out by Florian Adamsky at City University London, demonstrates how BitTorrent’s open protocols can be exploited to produce powerful DRDoS attacks. Some of the worlds most widely used BitTorrent programs, including Vuze, uTorrent and MainLine are vulnerable.
Distributed Denial of Service (DDoS) attacks use multiple compromised systems to attack a single target, consuming all of their resources and rendering the target unable to provide their service to normal users. BitTorrent is vulnerable to a similar attack named Distributed Reflected Denial of Service (DRDoS).
The DRDoS attacks exploit a weakness in BitTorrent’s open protocols. The vulnerable protocols include Micro Transport Protocol (uTP), Distributed Hash Table (DHT), Message Stream Encryption (MSE) and BitTorrent Sync (BTSync). The protocols are vulnerable to IP spoofing, which allows a sender to forge a false IP address. The DRDoS attack works by sending forged requests to a large number of vulnerable machines. The source address of the request is changed to the targets address, which means all of the replies will go to the target. Thus, reflecting all of the requests to the target.
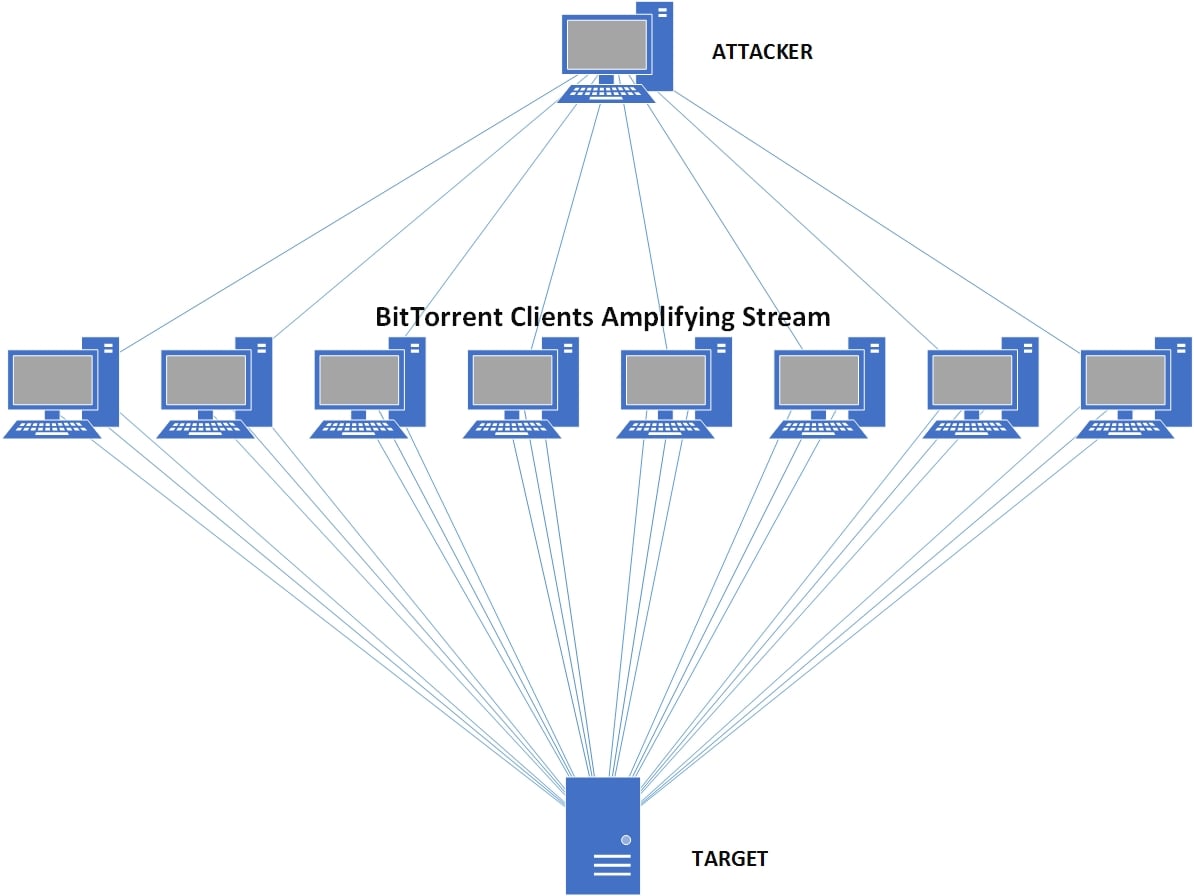
DRDoS attacks also typically involve amplification of the original request. This allows attackers to produce more bandwidth with fewer reflectors. In the paper, the researchers managed to exploit the open protocol handshakes to amplify the attack traffic from 50 to 120 times larger than the original request. This could potentially allow a single attacker to DDoS a large target without the use of a botnet.
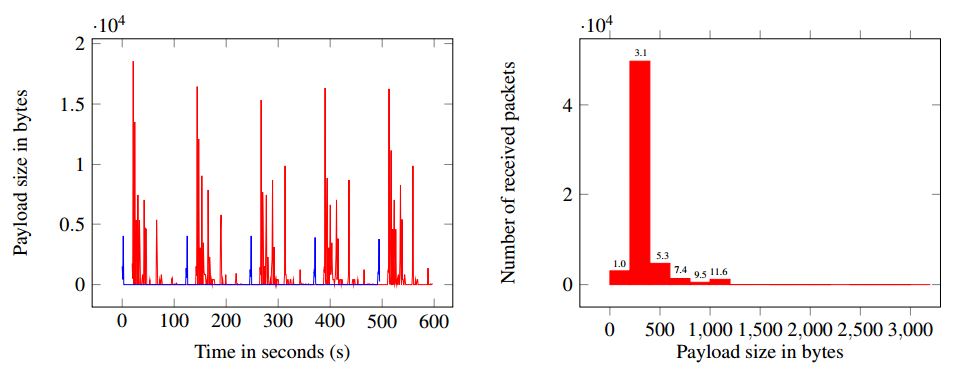
As well as the huge amplification of the requests, the DRDoS attacks via BitTorrent are not detectable by a firewall due to their dynamic port range and encryption during the initial handshake. To mitigate this kind of DDoS, deep packet inspection would be required, which consumes even more resources.
To demonstrate how robust and viable the attack was the researchers developed a BitTorrent crawler which ran over the period of one month and discovered more than 2.1 million vulnerable clients. BitTorrent has already been notified of the vulnerability and have reportedly released a fix in their latest Beta release, however, uTorrent and Vuze have yet to react.


Leave a Reply